Highlights from Digital Transformation World 2022

I attended the TM Forum’s Digital Transformation World in Copenhagen, Denmark, on 20−22 September 2022. Approximately 3,000 people attended, including many CSP and vendors executives. As an industry, although vendors continue to evolve their offers, many CSPs (with some notable exceptions in AT&T, China Mobile, China Unicom, and Vodafone, among others) have taken a breather the last few Covid-dominated years in their implementation of new technologies to scale, but now, unless recessionary forces and supply chain problems persist, will resume their formerly rapid pace of technological change.
Main Topics at Conference
- Network automation: It is becoming a matter of must do, not just good to do.
- 5G monetization: MNOs spent much on spectrum and network builds, how to recover the investment, and grow the business (mostly in enterprise).
- Digital transformation: Moving into the phase of doing it to scale but is hard to do, especially in a post-Covid, resource-constrained world.
My Primary Topics and Summaries
- Network automation and autonomous networks: Now considered much more important, with the leading equipment providers incorporating more operations functions into their physical and virtual network elements.
- The evolution of domain control and cross-domain orchestration systems: I released my first cross-domain orchestration market share document on Monday preceding the event and got many comments in this evolving area.
- Slicing: most CSPs are still stuck in the POC phase with over a dozen-and-a-half slicing managers offered by vendors, but commercial offerings are beginning.
- Automation, Analytics, and AI technology (A*A*A): Progressing nicely into real production.
- Disaggregated network elements: Not much happening at this event on this interest area. Come to Layer 123 in London in December to discuss.
Major Insights
Autonomous Networks have been proven by the leading CSPs (at least to Level 3 out of 5) in many use cases. The leaders are now moving to L3 to scale by 2023 and start pushing to Level 4 by 2025. With so many technicians in the CSPs retiring in the next five years and few younger employees, there is a great need to quickly automate the operations as much as possible.
MyTake: Few CSPs so far have adopted a goal of implementing even Level 3 autonomous operations, but the leaders have proved that it can be done and should be done. L4 by 2025 is a real stretch unless we accept a downgraded definition (is not well-defined) of L4. We will have the orchestration (i.e., initial provisioning part in reasonable shape, but the other part, where the network adjusts to maintain the original intent, even in the face of abnormal network events, will be some time in being implemented to scale. Some selected areas will have it, though.) The top 5% of CSPs are moving well along, the majority have yet to really make much progress. Vendors need to help the next group with their business cases and plans. The laggards will always be laggards, which may well be their downfall as their competitors provide services much cheaper and faster.
Digital transformation is a term that we have all heard. Every CSP thinks it needs to do it and are engaged in some variant of digital transformation in the BSS and OSS areas.
MyTake: Many people are getting tired of hearing about it, but the old rule of thumb in change management applies: “When people are sick and tired of hearing about the changes they need to make in the business, then you are halfway there in communicating the need to change.” Key areas of digital transformation are in portal interfaces (e.g., NaaS) to enterprise customers (with companies such as ServiceNow), ecosystem enablement (new areas such as Kloudville and the other digital marketplaces), billing of complex 5G and enterprise services (such as described by Ericsson, Oracle, Netcracker and others), and autonomous networks (with Huawei, Nokia, Ciena Blue Planet, and new entrants such as Itential leading the charge). Technological changes include the move to cloud-based computing, software control of the network, adoption of standard interfaces from the TM Forum (ODA), MEF, Broadband Forum, IETF, and others. Democratizing automation is being shown to be the best path for network automation, training the network engineers how to use low-code/no-code interfaces to create automation scripts, and bringing in the IT department for the more complex workflows within and across domains.
Intent-based interfaces between the customer, business, service, and resource layers are being discussed as necessary to move to layered autonomous networks where the control is pushed down as low as possible. Some progress has been made, but there is a lot to be done.
MyTake: We are going to have mostly template-based interfaces in production, not real intent-based interfaces. Full automated design, including complex error paths, will be only available in very selected areas. Maintaining the intent automatically will be even rarer in the next couple of years beyond areas we already know (e.g., moving connectivity paths at the IP and optical layers to get around network outages or degradation).
SaaS is being offered by many OSS and BSS vendors. Many have their entire product lines available as SaaS, and some higher-level functions are available only as SaaS.
MyTake: Selling SaaS for basic OSS and BSS functions is hard, except for new business or technical areas. The vendors will sell much more hybrid cloud implementations for the foreseeable future. I estimate that only about 25% of new OSS and 50% of new BSS deployments will be SaaS by 2027; obviously, embedded base numbers will be much lower.
Use-Case orientation for OSS and BSS software, rather than platform orientation. Many vendors of OSS and BSS, especially in the automation space, are adopting a business model that allows CSPs to buy and implement particular use cases, one at a time, on a common platform, rather having to buy and implement a platform and then configure the platforms for specific use cases (technically these days, there is not a tremendous difference, but business-wise the difference is huge). This approach is easier now because of the microservices nature of the software, where individual chunks of code can be written and installed, without others. This approach provides a good way for CSPs to match their business cases and their software purchases, delivers a low-cost initial implementation, and lays a growth path for the operator, while still providing the early-in vendors a strong incumbency position. Some use cases are offered optionally or even exclusively as SaaS.
MyTake: This is a very good direction. Some vendors, such as Netcracker and Ericsson, understood this years ago. Now others are catching on. It has been made much easier by the cloud-native nature of the software.
Disaggregated network elements have not become a topic of much discussion for this operations-focused conference.
MyTake: We will hear a lot more in the future about this. In the future, systems like the nonreal time RIC in distributed O-RAN systems will contain significant operations functions, some of which are now found in domain controllers or OSS systems.
Embedded network operations functions: A traditional strong first-cost selection model by CSPs’ procurement offices have hampered the vendors in embedding more operations capabilities into their equipment. This is changing. embedded security in routers (notably Nokia), functions for easier provisioning of PON access systems (notably Infinera), RF power-reduction management at the chip level (notably Qualcomm), and the integration of routing and optical transport (Cisco’s routed optical network) are good examples.
MyTake: I have been waiting for this day for 40 years. Full life-cycle costing is certainly still far away, but CSPs seem to be willing to spend a few percent more for their equipment to enable faster and less expensive operations with higher service quality.
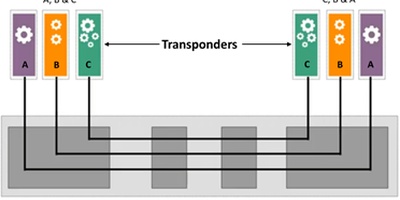
Slicing management: I have identified 17 slicing managers offered by vendors so far, providing the full set of PAID functions (provisioning, assurance, inventory, and design) necessary for life-cycle management of network slices. They are being offered as decomposable suites (see below).
MyTake: Slicing managers are pretty much all-in-one OSS systems. Will they become a product category? Unlikely, except in certain circumstances, but vendors are betting they can. I have a draft of a landscape report of these slicing managers and intend to publish it in my domain control and orchestrationresearch stream.
Decomposable suites: Most vendors now offer their OSS and BSS (as well as domain controllers, cross domain orchestrators and slicing managers) as suites of functions that can be ingested in toto or be implemented with one or more of its functions replaced with those from other vendors (or built by the CSPs themselves). We call these decomposable suites.
MyTake: We used to hear about the fight between best-of-suite multifunction solutions and best-of-class point solutions that needed to be integrated together. Those days are about over. The availability of reasonably well-defined standard interfaces by the TM Forum and other standard development organizations (SDOs)[1] along with microservices-based cloud-native software architectures allow us to have the best of both worlds.
Cross-domain orchestration and domain control: My recent cross-domain orchestrator market share document reveals the top 6 vendors in the space dominate, as expected by the independent software vendors who are intrinsically multivendor, usually working via southbound reasonably standard interfaces with domain controllers that mostly come from the network element vendors. Ciena Blue Planet, HPE, Itential, Netcracker, Nokia, and Sedona (Cisco) constitute the top 6 CDO vendors today.[2]
MyTake: Cross-domain orchestration is in its infancy. The current market is dominated by transport CDOs that orchestrate across the IP and optical domains, multilayer coordination. These are solving real problems today. The excitement of the future will come from the newer areas such as access plus MEC (called edge by some vendors), slices across the entire end-to-end mobile network, and slices that include data center resources, among others. Stay tuned for the CDO forecast as well as the transport domain control market share coming out soon (available to subscribers or as single-copy sale).
For more information, contact Mark Mortensen, mmortensen@acgcc.com.
____________________________________________________________________________
[1] In the past I would not have characterized the TM Forum, the Metropolitan Ethernet Forum, the Broadband Forum or the IETF, and many others as SDOs. Those terms were reserved for formal government-recognized organizations such as ETSI, the ITU, and ANSI. However, most of the best standards work is now going on in those industry-enabled organizations, then adopted later as official standards. Thank you, IETF, for showing us all the way to achieve standards quickly—requiring reduction to practice during the proposals—and moving quickly. And thank you, hyperscalers, for leading the way toward cloud-native architectures, bringing the best of service-oriented architectures to the internals of software systems by exposing APIs everywhere between microservices. It requires profligate use of computation and storage resources, but so what? It is so much easier to write, deploy, and evolve (via DevSecOps development and deployment methodologies with CI/CD processes).
[2] Mortensen, Mark H, Highlights: Cross-Domain Orchestration Market Shares, September 2022. https://www.acgcc.com/reports/highlights-cross-domain-orchestration-market-share/ The full report, including a market size and forecast, will be available in October for subscribers to the ACG Research Domain Control and Orchestration research stream, as well as sold in a single copy format.